Project Euler has been taken down after a security breach. There is no indication of when — or even if — the site will return. All that’s left is the following message:

What sort of lowlife scumbag would attack a site like this?
Project Euler has been taken down after a security breach. There is no indication of when — or even if — the site will return. All that’s left is the following message:

What sort of lowlife scumbag would attack a site like this?
The latest HackerRank weekly challenge attracted 71 entries from the US and 387 from India, but only four from the UK. I think this is the lowest turnout so far. Maybe the good weather had something to do with it.
But anyway, I’m still quite pleased with coming in 1st out of the UK contingent and 52nd (out of 720) overall. My solution to the GCD product question could have been speeded up, and I would probably have made the effort if my first solution hadn’t passed all the test cases in a matter of milliseconds.
Oh well.
Untrusted is a Javascript adventure game where the only way you can win is by rewriting parts of its source code as you go along. For example, in the very first level, your character (a simple “@” character) is imprisoned inside four walls (represented by “#” characters). To reach level 2, you have to edit the code that creates the walls. Simply deleting it will do the trick, as shown here:
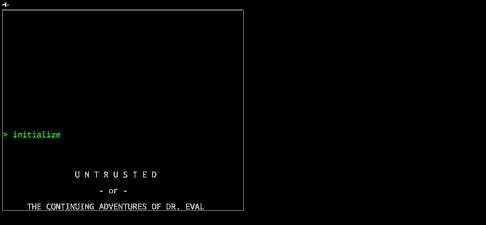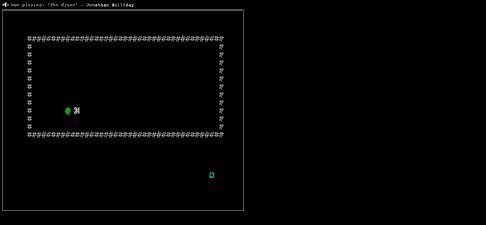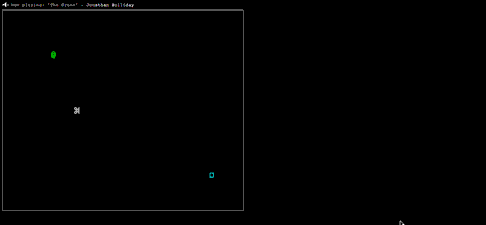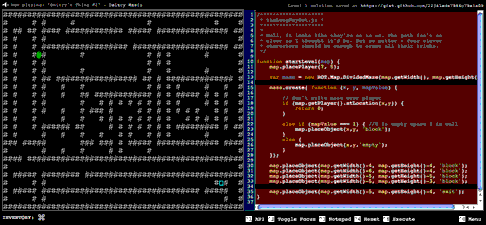
But it soon gets much more complicated. There are 22 levels in all — level 22 just displays the end credits, but it took me a little while to figure out how to get there. The game’s backing music is quite good, too.
I recently learned about an encryption protocol called CipherSaber, which was developed in 2001 by author, consultant and Star Wars fan Arnold G. Reinhold in retaliation against government plans to restrict access to strong cryptographic techniques.
CipherSaber is based on a stream cipher called RC4 (a.k.a. “Arcfour”) that was developed by Ron Rivest. Since the RC4 algorithm is simple enough for a programmer to implement from memory, it is effectively immune to any sort of software embargo.
Although CipherSaber lacks important features like a key exchange mechanism and cryptographic techniques have moved on since 2001 (RC4 is no longer considered entirely safe), CipherSaber is still a useful cipher of last resort. I’d encourage anyone with an interest in cryptography or programming to try their hand at creating their own implementation. Reinhold’s pages are starting to show their age (broken links everywhere!), so I’ll summarize the algorithm below:
You will need:
num_rounds which should equal 1 for the original CipherSaber algorithm, or 20 for CipherSaber-2 (recommended). Or you can choose some other value if you like.S and S2.S by filling it with all the values from 0 to 255 (i.e., S[0]=0, S[1]=1, S[2]=2, and so on.)S2.S2, directly after the secret key. Then fill up the remainder of S2 by repeating the secret key and initialization vector until you have set all 256 positions in S2.S based on the contents of S2. This is done by swapping bytes in S according to the following method, using the value of num_rounds you chose earlier:
j = 0
for n in (1 .. num_rounds)
for i in (0 .. 255)
j = (j + S[i] + S2[i]) mod 256
swap S[i], S[j]
end
end
You can now discard S2; it won’t be used any more.
S to generate a pseudo-random stream of bytes to combine with the input data (using exclusive-or (XOR) operations). Since this is a symmetric cipher, the procedure is exactly the same for encryption and decryption:
i = 0; j = 0
for each byte b of binary data:
i = (i + 1) mod 256
j = (j + S[i]) mod 256
swap S[i], S[j]
k = (S[i] + S[j]) mod 256
output (b xor S[k])
end
Well I hope that isn’t too complicated. Frankly it’s about at the limit of what I’d be able to reproduce from memory, and I’m not sure I’d be able to get it right first time either. But do have a go at writing your own. You’ll probably want somewhere to test your code, and for that purpose I’ve set up an online encryption/decryption tool that you’re welcome to use.
And finally, don’t forget to use a strong password with CipherSaber. Here’s a text encrypted with CipherSaber-2 using one of the 25 most common passwords of 2013. See if you can figure out what it was:
f8 a2 76 5d d2 3a 75 67 0f 15 ea 1e 8d 55 9f 39 69 cd 3f d6 61 48 06 85 65 1e a3 1a eb d7 88 dd d8 cd 46 e8 0c d6 cd 2d b1 bf 7b 34 aa fc aa ed 39 a9 14 6f e7 5c 57 f6 23 f8 69 d3 17 f7 0a f8 a8 7d 29 f3 9c e7 45 51 0d 6c 92 b8 9f 3d 6c 5a c8 8c 7d 71 e0 60 75 fb 00 61 c6 f2 02 60 e3 38 ab c0 48 f7 ed bd 05 67 c0 25 99 cc 85 67 23 ae 67 61 e2 0c ce 90 95 c8 8a 9f 19 ca 2e 35 0b a8 c3 31 6a 39 3a 24 52 31 e4 81 ae 35 f6 d9 c7 5f 31 3e 6f 2f 2f 96 87 95 0c 2f 90 87 1f a2 94 68 e3 ac 93 29 4d a7 53 24 a1 ca 51 35 10 84 50 58 01 12 42 6a 6a 0b f4 1d a6 33
A marvellous bit of science here from professor Roger Bowley:
At half past ten tonight (about ten minutes from now) it will be exactly 36 years since the first episode of The Hitchhiker’s Guide to the Galaxy was broadcast. To mark the occasion, the BBC is not only repeating the entire series on Radio 4extra, but has also published some clips from other programs where the series was discussed. Here’s one where Douglas Adams describes how he arrived at the name Slartibartfast for one of the characters:
I don’t think I’ve ever found the arrival of a new programming language worth getting excited about. But this really does look interesting:
If anyone ever gets round to creating a real Hitchhiker’s Guide to the Galaxy, this is the sort of language they’ll be using.
Close-up view of an LCD monitor showing the letter “e” rendered with (top) no antialiasing, (middle) traditional antialiasing, and (bottom) subpixel antialiasing. (Credit: ALexL33 @ Wikimedia Commons)
Subpixel rendering is the technique your computer uses to make text on the screen as readable as possible even at small font sizes.
In a typical LCD monitor, each pixel is represented by a combination of three separate light-emitting elements, which are coloured red, green and blue. When they are all switched on, the pixel appears white, and when they are all switched off, the pixel appears black. Other colours can be displayed by varying the red, green and blue components individually, and for shades of grey, these components are always equal.
To display smooth lines and curves, a technique called antialiasing is used to eliminate the jagged edges that appear where dark and light pixels are placed adjacent to each other. This is illustrated in the middle of the image on the right, where the pixels forming the letter “e” have been changed to smoothly varying grey levels to avoid the jagged appearance of the non-antialiased letter at the top of the image.
Subpixel antialiasing goes one step further by working on the transitions between individual light-emitting elements instead of at the pixel level. This is done by applying a reddish or bluish hue to pixels to adjust the brightness at the edges of each RGB pixel.
After reading a recent question at Stack Overflow, I got to wondering how easy it would be to reverse this subpixel rendering process on antialiased text. This might, for example, be useful if you’re trying to use OCR software to read text from a screenshot image.
Here’s an example of text grabbed from my computer monitor (scaled up 300%):

If you look closely, you can see that the letters are coloured red on the left and blue on the right due to the effects of subpixel antialiasing:
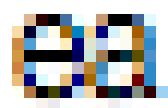
OCR software often uses thresholding to separate text from background details. Applying a simple 50% threshold filter to this antialiased text gives illegible results:

Although this can be improved by choosing the threshold value more carefully, I got much better results by writing some software to scale up the original image while taking subpixel antialiasing effects into consideration. This is what I got:

If you think it might be useful, you can download the software here: subpix.c. It uses the GD graphics library, but it shouldn’t be too hard to make it work with other libraries.
B3ta.com has been offline all evening. This is not such bad news, as there are other things I should really be doing right now.
It would be nice, however, if my computer could let me know when the site comes back to life. I wrote a quick bash script to do this for me, so I thought I’d share it. This script tries to download a web page every five minutes, and when it succeeds, it will tell you the website has come back online and open the page in your browser.
If you’re not using OS X, you might have to make a few changes to get the text-to-speech announcement working and to open the web page in your browser. I’m sure it won’t be too difficult.
#!/bin/bash # # Poll a website until it comes back online, then open it in # the default web browser. # # Edit the following two lines: URL="http://www.b3ta.com/board" TITLE="The b3ta board" # until [ "`curl -s --connect-timeout 5 --head $URL 2>/dev/null`" ]; do sleep 300 done say "$TITLE is back online" open $URL
Before anyone says anything — yes, I know it could be improved. I should at least check for a 200 OK response code. But this will do for the time being; the b3ta server isn’t even responding to pings at the moment.